Citrix ShareFile
The target's corporate Citrix ShareFile service emails them a link to a malicious file.
Methods
Payloads
Goals
Description
Lots of corporations use file shares, such as Citrix ShareFile. In this pretext, an attacker spoofs an email from the target company's Citrix ShareFile service to an employee. The email is sent from a generic role-based email address, like "docs@company.com". In the email, the attacker shares a link to an enticing file, such as "Sales Memorandum" or "Salary Renegotiation Process". The email could identify a colleague that shared the file with them or exclude that information. When the victim clicks on the link, it takes them to a phishing site where the attacker could harvest credentials or conduct a drive-by-download attack. Alternatively, it could be a direct download of an office file containing macros. We recommend sending an HTML-based email that looks very similar to an official Citrix ShareFile email. Please see the resources at the end of the page for email design.
Example Email(s)
From: Documents
Subject: You have an encrypted message
Download
Trouble with the above link? You can copy and paste the following URL into your web browser:
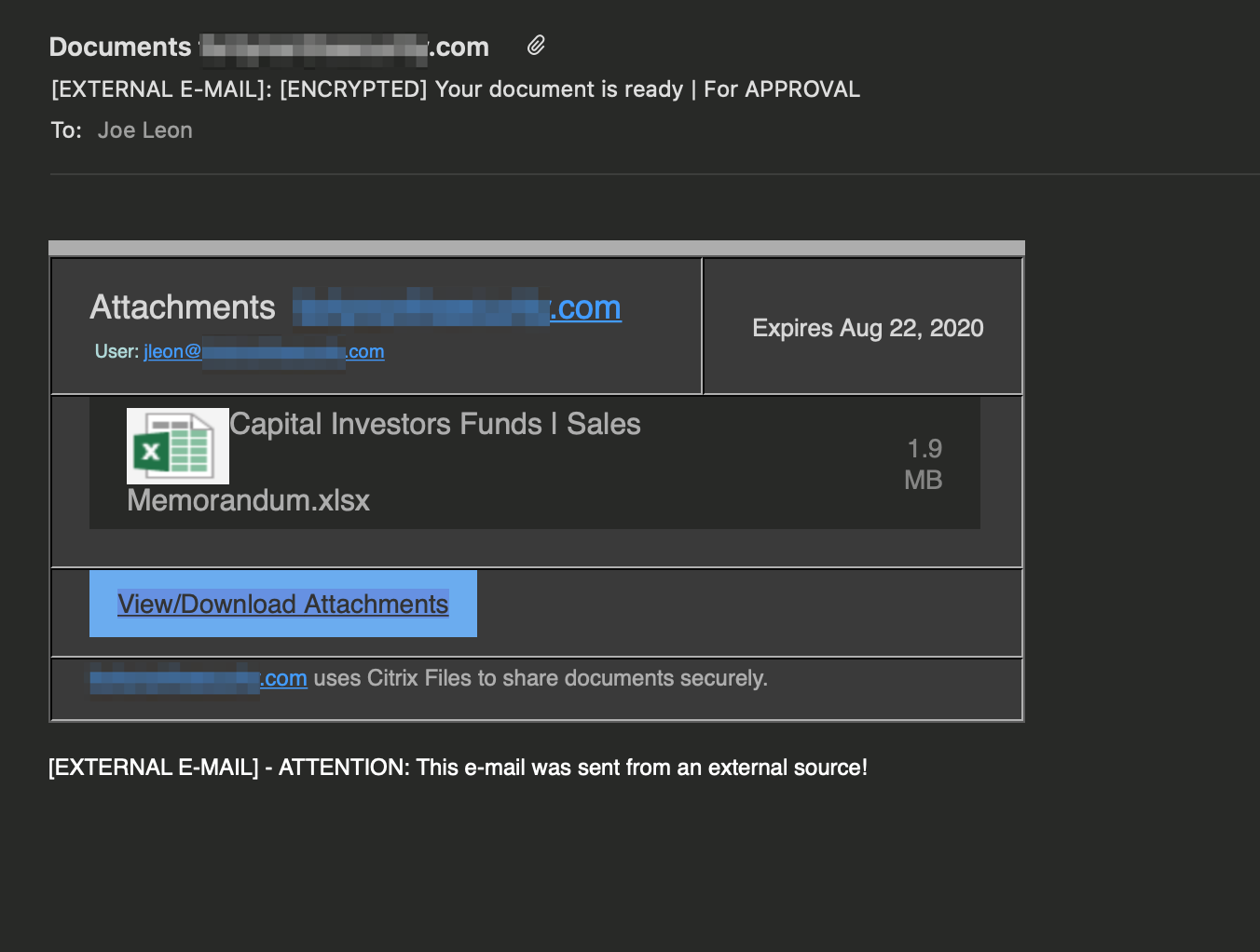
Source: https://twitter.com/joeleonjr
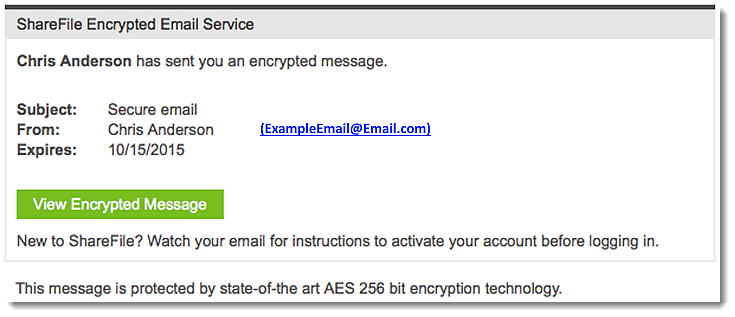
Source: https://support.citrix.com/article/CTX208306
Example Payload Ideas
Fake Citrix ShareFile login portal or fake VPN login portal asking target for their credentials. If used with a tool like Evilgnx2, you could also circumvent multi-factor authentication and hijack their session.
User tries to visit the juicy or interesting link and instead hits a page that either displays a fake file, or if you want to invest less time, you could send them to a page that says "this file no longer exists", or "you are not authorized to view this file". From there, a drive-by-download attack occurs.
Fake file with XLM (Excel 4.0) macros.
Analysis
When you receive an email with a file that you plausibly could expect or a file that seems to contain juicy information, an employee might click on the link to view the file without conducting sufficient due diligence.